Download What Is Web Application Explain The Vulnerabilities In Web Application developed for efficiency and performance. Perfect for trainees, specialists, and hectic households.
From basic daily plans to comprehensive weekly layouts, our templates help you remain on top of your concerns with ease.
What Is Web Application Explain The Vulnerabilities In Web Application

What Is Web Application Explain The Vulnerabilities In Web Application
Keep up with Michigan Wolverines Football in the 2024 season with our free printable schedules Includes regular season games Schedules print on 8 1 2 x 11 paper Full 2024-25 Michigan Wolverines schedule. Scores, opponents, and dates of games for the entire season.
2021 Football Schedule University Of Michigan Athletics

Vulnerability Assessment Lanworks
What Is Web Application Explain The Vulnerabilities In Web ApplicationMichigan Wolverines. Location: Ann Arbor, MI. Stadium: Michigan Stadium. Capacity: 107,601. Mascot: None. Conference: Big Ten. 2024 Record: 5-4, 3-3 (Big Ten) 2024 Schedule. Future. The official 2024 Football schedule for the Michigan Wolverines
Here is the Michigan Wolverines football schedule for the 2023 season with opponents game locations game times and TV channels Understanding Cyber Attacks Across OSI Layers Safeguarding Your Network The official 2022 Football schedule for the Michigan Wolverines.
Michigan Wolverines Schedule 2024 25 NCAAF Games
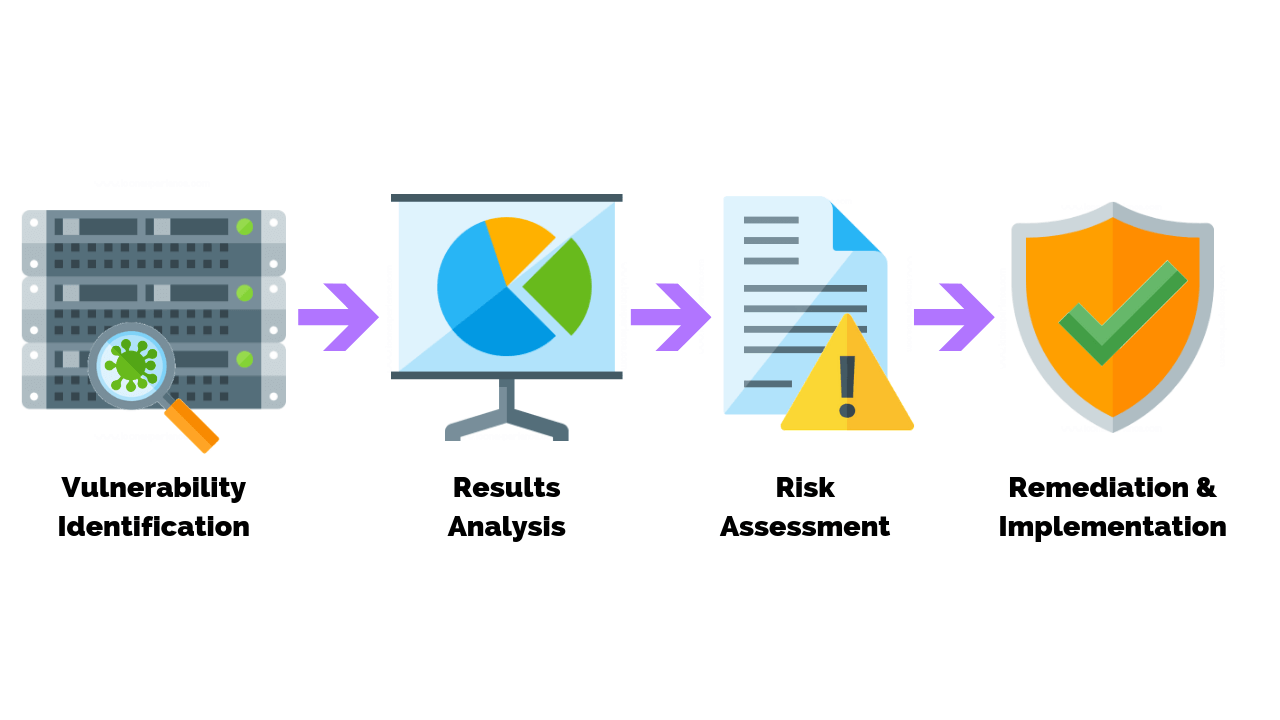
What Is Vulnerability Assessment CyberSecuriosity Professional
Michigan football schedule 2024 TV channels dates start times Week 1 Aug 31 vs Fresno State 7 30 p m NBC Week 2 Sept 7 vs Texas 12 p m Fox Watch on Fubo with 7 day free Certified Ethical Hacker CEH Vulnerability Analysis The Hacker Tips
2021 Football Schedule vs Northwestern Nov 23 Sat TBA Buy Now 70 Tickets From 70 160 Northwestern on November 23 TBA Future Michigan Football Schedules Michigan Software Component Vulnerabilities Veracode Overview Of Web Application Security Red Piranha

Common Web Application Vulnerabilities Indusface Blog
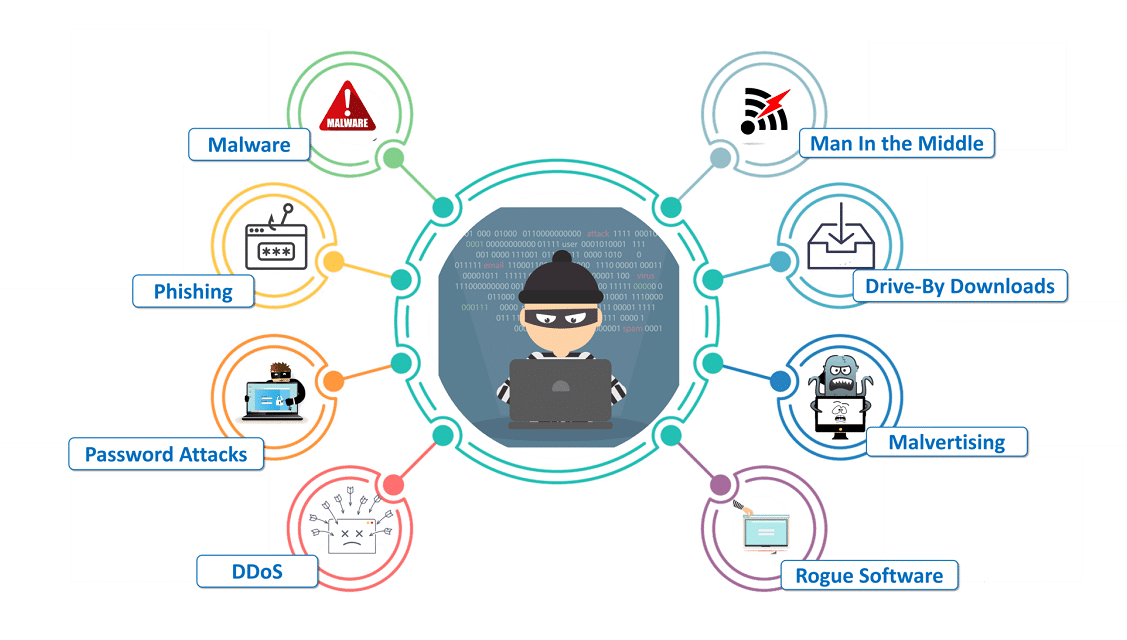
Web Application Security Best Practices EiqnetWorkS
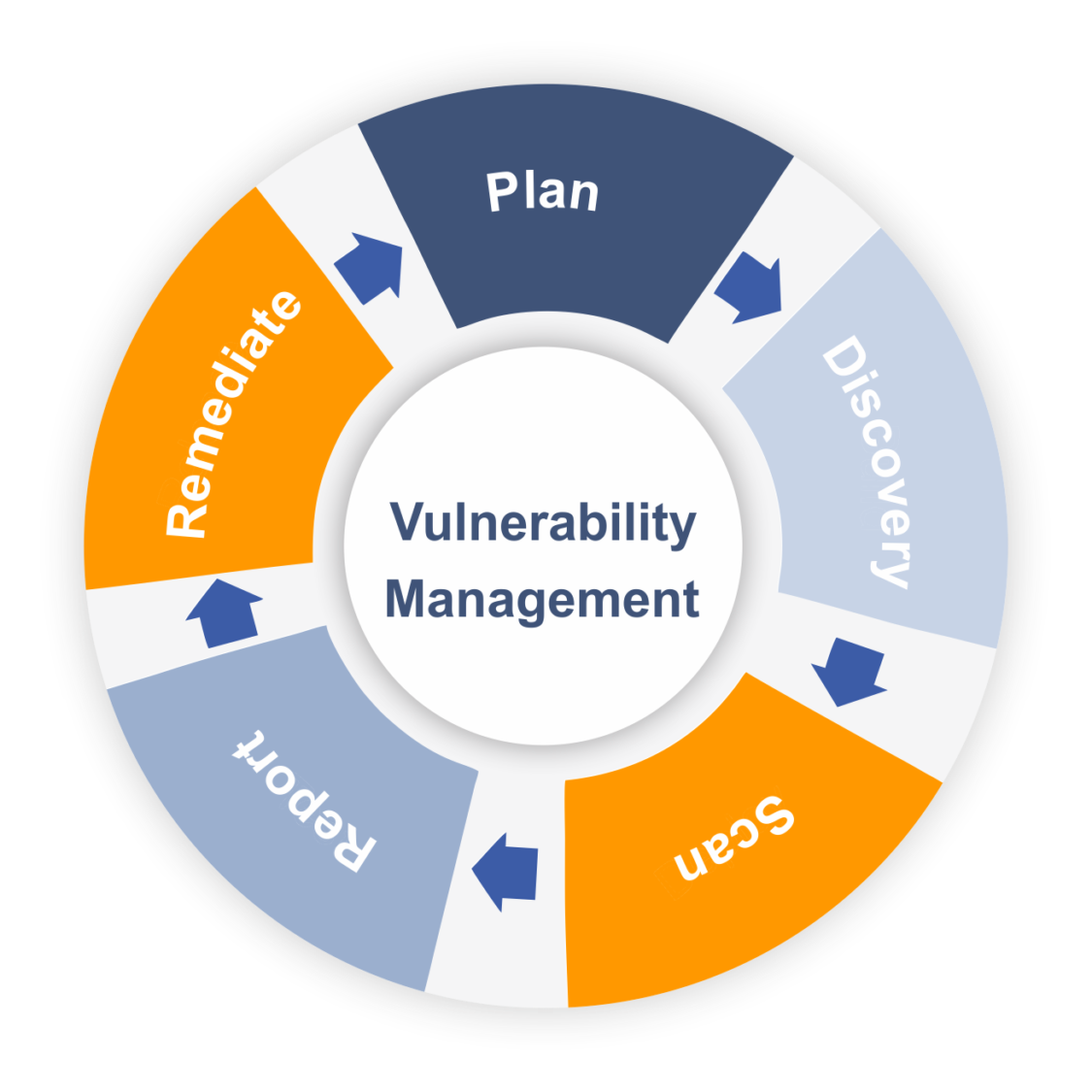
Vulnerability Assessment Scanning Tools List 2018 ESecForte
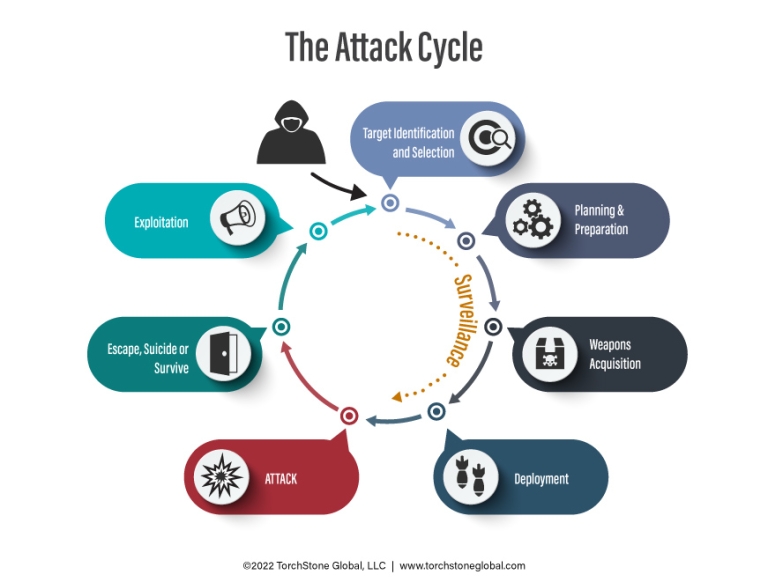
Attack cycle diagram TorchStone Global

Onsite Or Remote Vulnerability Assessment Services

25 Simplicity Pattern 1035 SaharaNusa

9 Best Practices For Web Application Security
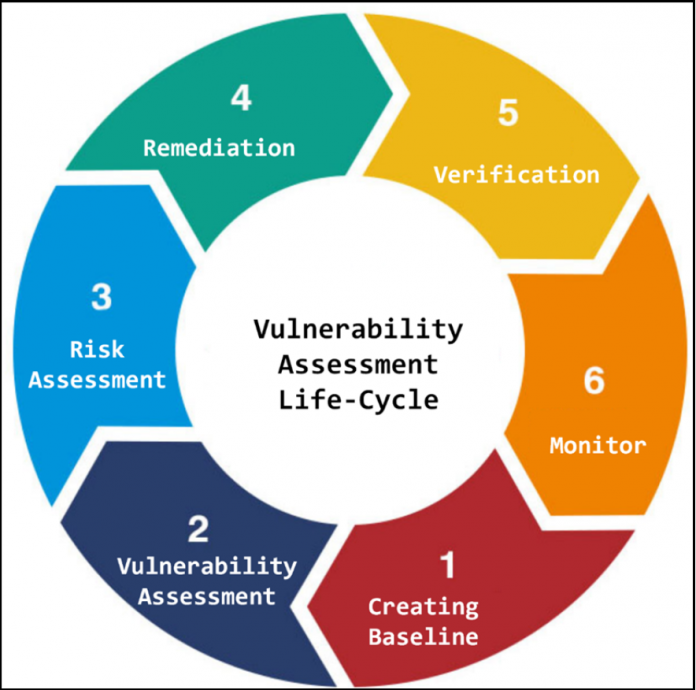
Certified Ethical Hacker CEH Vulnerability Analysis The Hacker Tips

Creating A Vulnerability Management Strategy ZSecurity
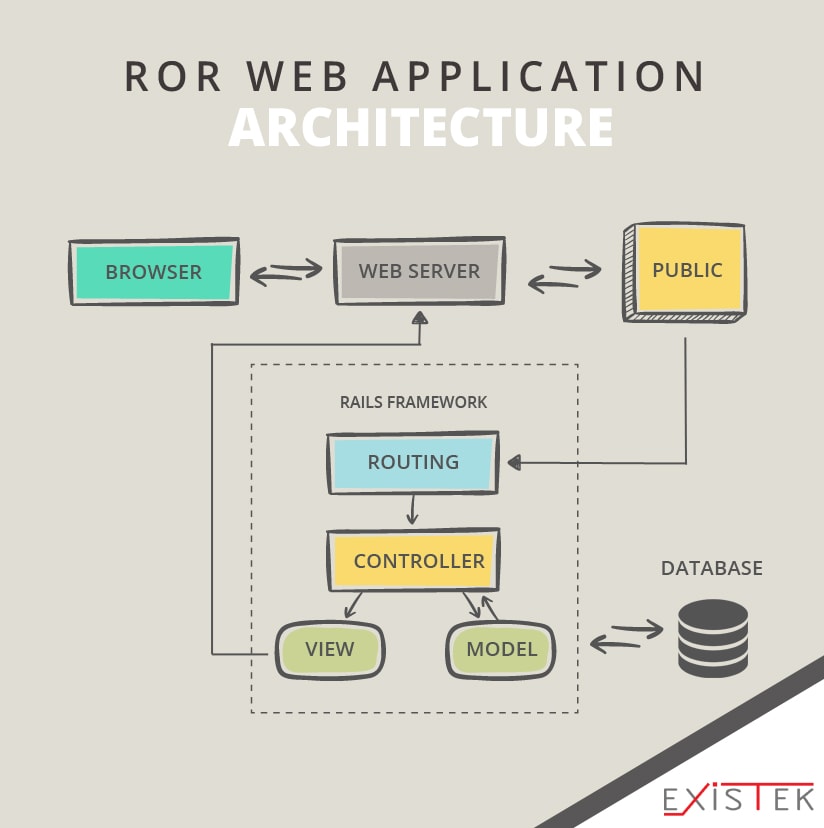
Web Application Architecture Existek Blog